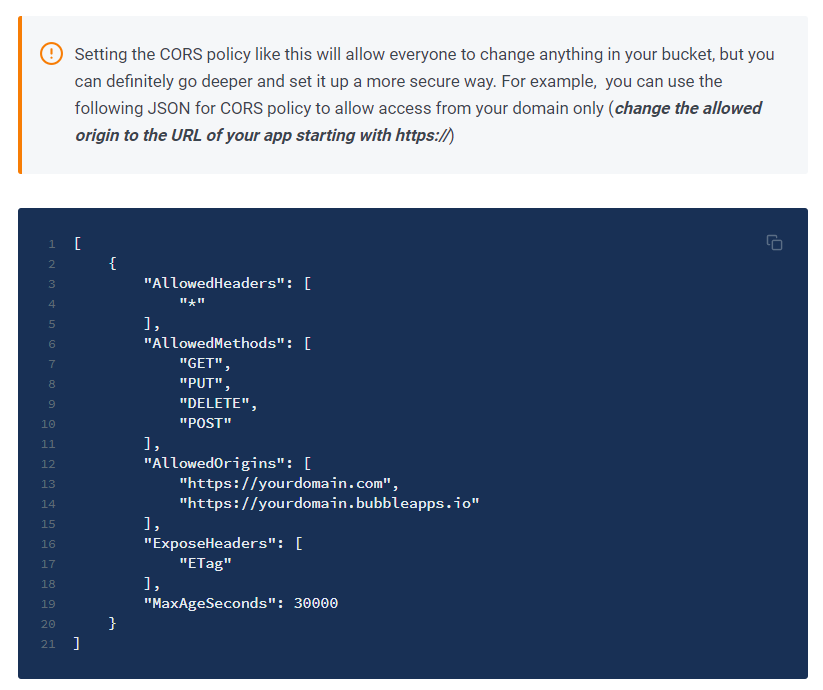
Below is an email I received from Amazon. How come I set up the Zeroqode AWS plugin according to instructions and now AWS wants to write me warning letters? Is Zeroqode doing something wrong that AWS doesn’t like or what?
Lately there seems to be too much Amazon focus and attention on the Zeroqode plugin relating to SSL certificates and now too much traffic by public ?
Whats the story?
Hello,
We are writing to notify you that you have configured your S3 bucket(s) to be publicly accessible, and this may be a larger audience than you intended. By default, S3 buckets allow only the account owner to access the contents of a bucket; however, customers can configure S3 buckets to permit public access. Public buckets are accessible by anyone on the Internet, and content in them may be indexed by search engines.
We recommend enabling the S3 Block Public Access feature on buckets if public access is not required. S3 bucket permissions should never allow “Principal”:"*" unless you intend to grant public access to your data. Additionally, S3 bucket ACLs should be appropriately scoped to prevent unintended access to “Authenticated Users” (anyone with an AWS account) or “Everyone” (anyone with Internet access) unless your use case requires it. For AWS’s definition of “Public Access,” please see The Meaning of "Public” [1].
The list of buckets which can be publicly accessed is below:
NAME WITHHELD* | us-east-2
You can ensure individual buckets, or all your buckets prevent public access by turning on the S3 Block Public Access feature [2]. This feature is free of charge and it only takes a minute to enable. For step by step instructions on setting up S3 Block Public Access via the S3 management console, see Jeff Barr’s blog [3], or check out the video tutorial on Block Public Access [4].
If you have a business need to maintain some level of public access, please see Overview of Managing Access [5] for more in-depth instructions on managing access to your bucket to make sure you’ve permitted the correct level of access to your objects. If you would like more information about policy configuration in S3, please refer to Managing Access in Amazon S3 [6], and S3 Security Best Practices [7].
We recommend that you make changes in accordance with your operational best practices.
If you believe you have received this message in error or if you require technical assistance, please open a support case [8].
[1] https://docs.aws.amazon.com/AmazonS3/latest/dev/access-control-block-public-access.html#access-control-block-public-access-policy-status
[2] https://docs.aws.amazon.com/AmazonS3/latest/dev/access-control-block-public-access.html
[3] https://aws.amazon.com/blogs/aws/amazon-s3-block-public-access-another-layer-of-protection-for-your-accounts-and-buckets/
[4] https://aws.amazon.com/s3/features/block-public-access/
[5] https://docs.aws.amazon.com/AmazonS3/latest/dev/access-control-overview.html#access-control-resources-manage-permissions-basics
[6] https://docs.aws.amazon.com/AmazonS3/latest/dev/s3-access-control.html
[7] https://docs.aws.amazon.com/AmazonS3/latest/dev/security-best-practices.html
[8] https://aws.amazon.com/support
Sincerely,
Amazon Web Services
Amazon Web Services, Inc. is a subsidiary of Amazon.com, Inc. Amazon.com is a registered trademark of Amazon.com, Inc. This message was produced and distributed by Amazon Web Services Inc., 410 Terry Ave. North, Seattle, WA 98109-5210