Hello there,
I am new to AWS but I want to ensure maximum security for our S3 bucket when using the AWS S3 uploader.
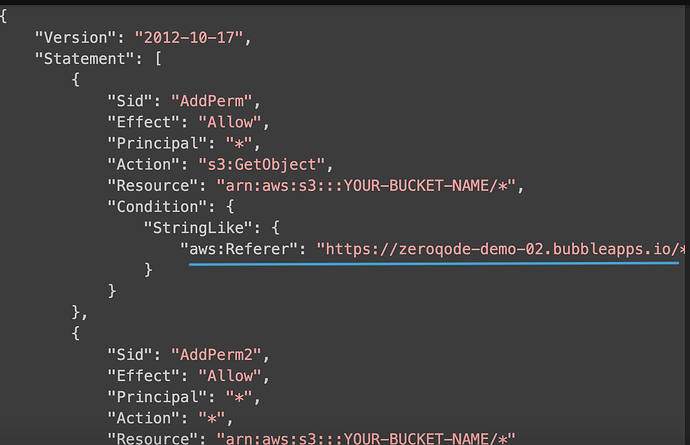
When following the documentation, I don’t really understand why they added the statement with the id “AddPerm”.
From my understanding, statement “AddPerm2” will always evaluate to true and therefore this policy will always apply.
And did I understand that correctly that the bucket policies is checked first and then the CORS or can you not relate those two in such a way. So my question is what the use case is for “AddPerm”?
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AddPerm",
"Effect": "Allow",
"Principal": "*",
"Action": "s3:GetObject",
"Resource": "arn:aws:s3:::YOUR-BUCKET-NAME/*",
"Condition": {
"StringLike": {
"aws:Referer": "https://zeroqode-demo-02.bubbleapps.io/*"
}
}
},
{
"Sid": "AddPerm2",
"Effect": "Allow",
"Principal": "*",
"Action": "*",
"Resource": "arn:aws:s3:::YOUR-BUCKET-NAME/*"
}
]
}
Any help is very much appreciated!
Best
Annabell