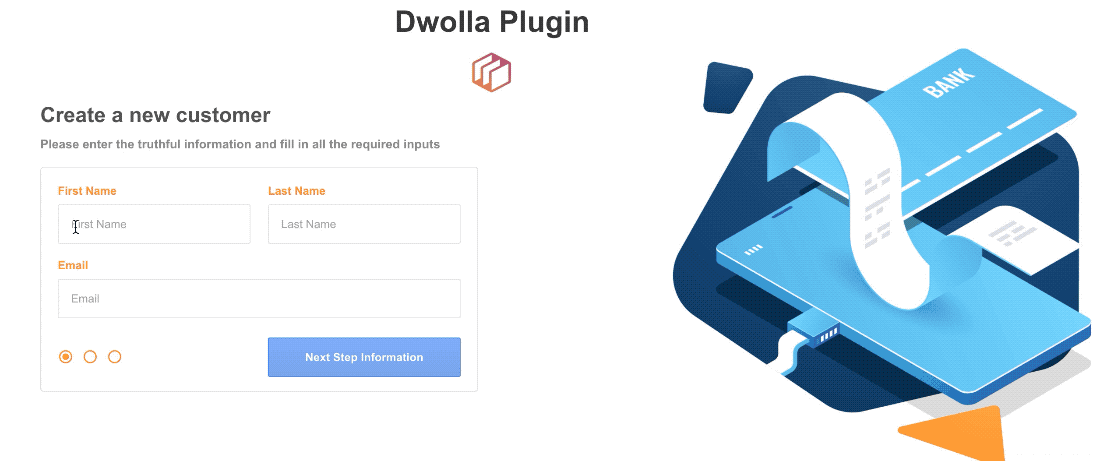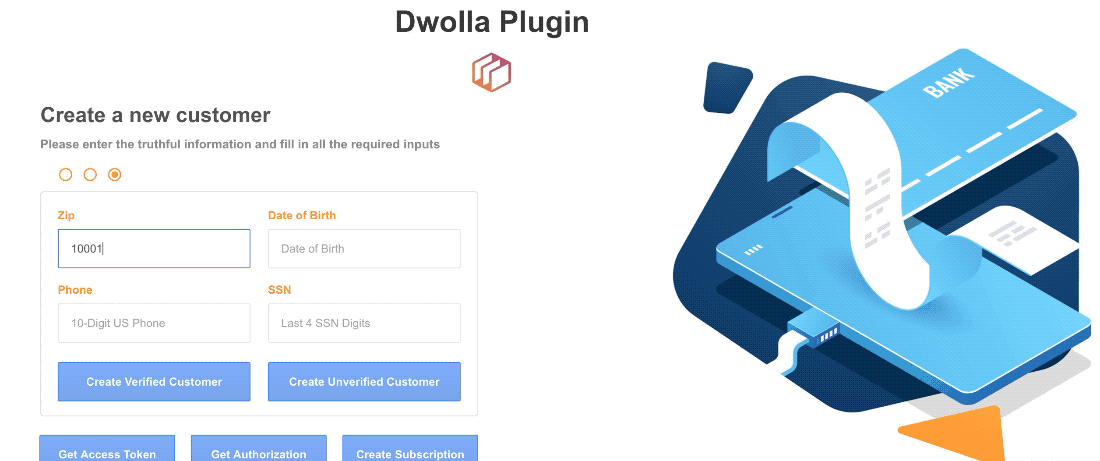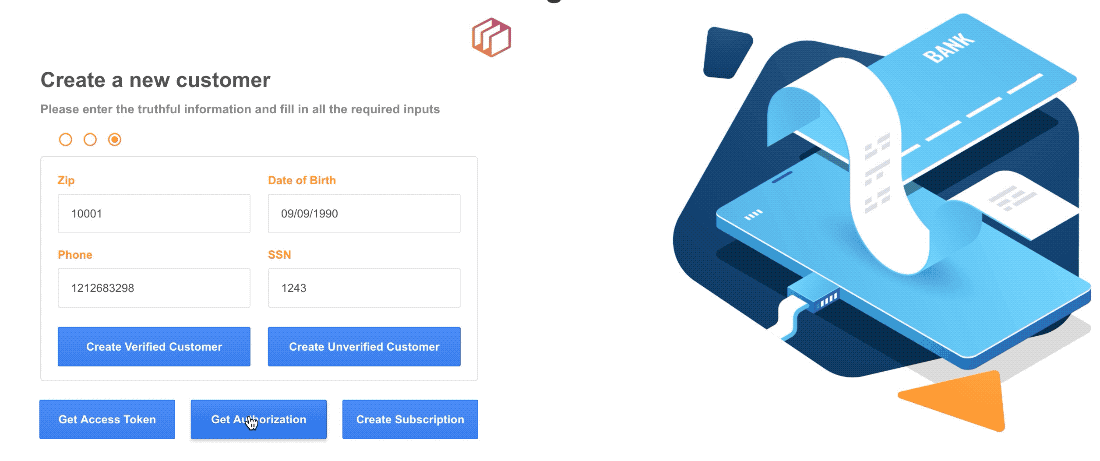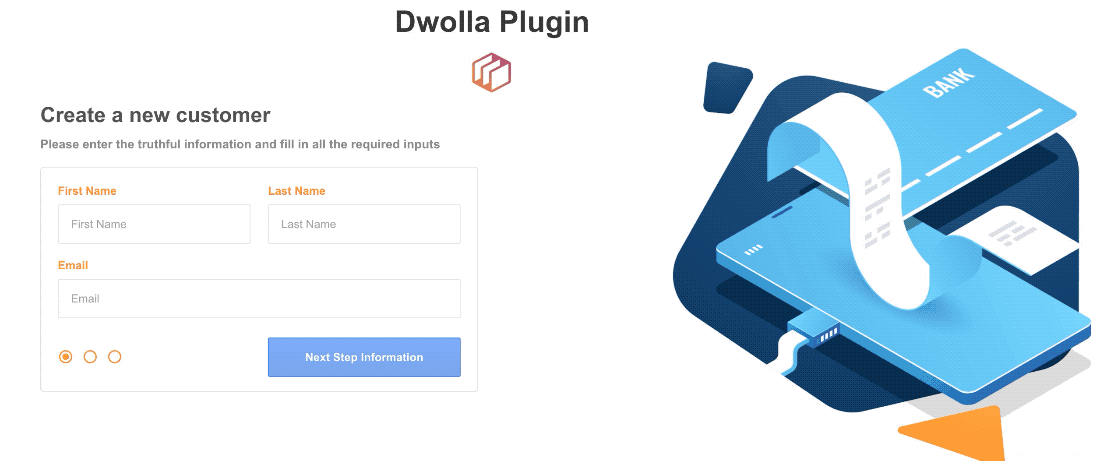
Thanks, @alex.grimacovschi. Here is what I heard back from Dwolla.
After reviewing your use-case and the previous client who has utilized bubble, we were unfortunately unable to find any evidence or cause to lower or accept the risk-based upon their password hashing procedures. However, we also weren’t able to confirm via Bubble’s official documentation that the SHA256 scheme you provided in the questionnaire is Bubble’s current practice.
They have had one other client try and connect using Bubble but were unsuccessful. For alternatives, this is what they responded with.
The other options largely center around offloading your authentication flow outside of bubble. That would likely require a small tech lift and/or further plugin purchases on your end. We can certainly talk about this more if desired but as these options have the highest added tech debt I recommend we proceed by reaching out to bubble for confirmation of their practices first.
We are going back to confirm if Auth0 would meet your standards. I just thought I would keep you and @levon update so you can update the plugin docs once we find out more.
Best,
Cole