Hello:
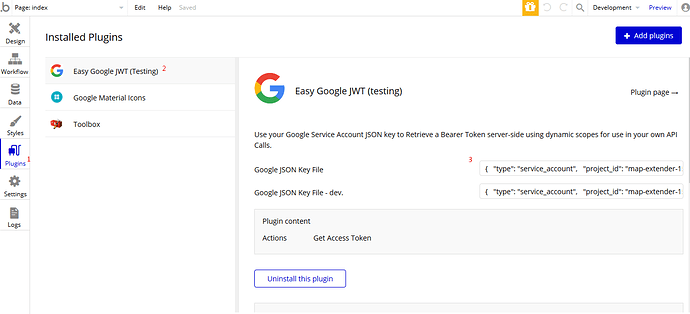
I purchased this plugin of yours, https://bubble.io/plugin/easy-google-jwt-1553988006484x522148132142186500, to make my life simpler with Google.
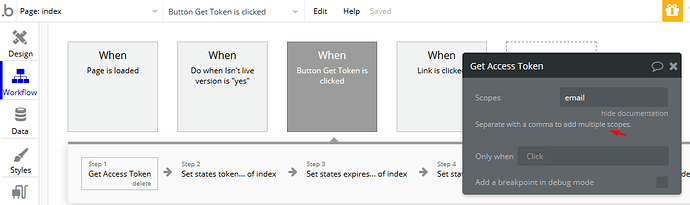
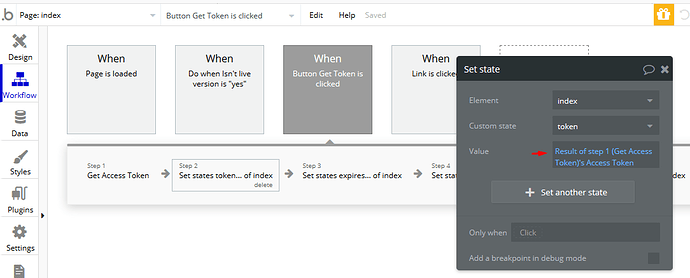
The instructions are pretty unclear. How do I go about making the new calls using the returned bearer token?
I.e.: how do I setup the API Connection using Bubble’s API Connector plugin.
Such as: which authentication type, etcetera.
Thanks